Themida by Oreans provides a vast list of protection mechanisms.
I'll explain a very simple approach to defeating Themdia 2.x protection schemes using Qemu, Universal Import Fixer, and Imports Fixer 1.6.
Qemu was the only virtual environment that this Themdia protected exe did not detect and would run in completely. It did an excellent job detecting IDA (even with IDA Stealth) and would not run inside Immunity Debugger.
It also has built in kernel debugging detection. The binary will execute in Vmware, however it doesn't execute its true payload inside Vmware.
Needed for this tutorial are:
- Qemu running XP
- Universal Import Fixer
- Imports Fixer 1.6
5U4N8Q..exe (Malware_5u4n8Q.zip) is the target file we will be unpacking. (Samples not provided)

1) Inside of Qemu double click on 5U4N8Q..exe , open taskmgr and get its PID.

2) Open Universal Import Fixer v1.2, enter the PID (deselect hex), and make sure Fix Directly Imports is checked and click Start
In the log window you'll see UIF finding all the indirect API calls. Take note of the IAT RVA the IAT SIZE and the New IAT VA from UIF

Below is output from the log file (the full log file is attached below as UIF-Log.txt):
Log File
===============================================================
Fixing : 5u4n8Q..exe
Code Start : 00000000 -> Auto: 00400000
Code End : 00000000 -> Auto: 009C5000
New IAT VA : 00000000 -> Auto: 03910000
Fix Directly Imports : Yes
===============================================================
5u4n8Q..exe
00400000 to: 009C5000
Target Module,Skipped...
ntdll.dll
7C900000 to: 7C9B0000
00402714: Directly-> 03910000 : 7C901005 : RtlEnterCriticalSection
0040271C: Directly-> 03910004 : 7C9010ED : RtlLeaveCriticalSection
0040C700: Directly-> 03910000 : 7C901005 : RtlEnterCriticalSection
0040C92C: Directly-> 03910004 : 7C9010ED : RtlLeaveCriticalSection
kernel32.dll
7C800000 to: 7C8F4000
004027A4: Directly-> 03910008 : 7C81CAA2 : ExitProcess
0050A119: 0061F0E4-> 0391000C : 7C810C21 : GetFileSizeEx
----Truncated------------------------------------------------------
xpsp2res.dll
20000000 to: 202C5000
Not Found any Exports...
===============================================================
Fixing Success...
Fixed Module : 5u4n8Q..exe
Image Base : 00400000
IAT RVA : 03510000
IAT Size : 00000410
Normal Imports : 38
Directly Imports : 234
All Imports : 272
===============================================================
===============================================================
Fixing : 5u4n8Q..exe
Code Start : 00000000 -> Auto: 00400000
Code End : 00000000 -> Auto: 009C5000
New IAT VA : 00000000 -> Auto: 03910000
Fix Directly Imports : Yes
===============================================================
5u4n8Q..exe
00400000 to: 009C5000
Target Module,Skipped...
ntdll.dll
7C900000 to: 7C9B0000
00402714: Directly-> 03910000 : 7C901005 : RtlEnterCriticalSection
0040271C: Directly-> 03910004 : 7C9010ED : RtlLeaveCriticalSection
0040C700: Directly-> 03910000 : 7C901005 : RtlEnterCriticalSection
0040C92C: Directly-> 03910004 : 7C9010ED : RtlLeaveCriticalSection
kernel32.dll
7C800000 to: 7C8F4000
004027A4: Directly-> 03910008 : 7C81CAA2 : ExitProcess
0050A119: 0061F0E4-> 0391000C : 7C810C21 : GetFileSizeEx
----Truncated------------------------------------------------------
xpsp2res.dll
20000000 to: 202C5000
Not Found any Exports...
===============================================================
Fixing Success...
Fixed Module : 5u4n8Q..exe
Image Base : 00400000
IAT RVA : 03510000
IAT Size : 00000410
Normal Imports : 38
Directly Imports : 234
All Imports : 272
===============================================================
End of Log File
3) Open Imports Fixer 1.6, highlight the 5u4n8q..exe process, right click on it and select Dump. In the Dumper Tool window select Dump

Save the file as 5u4n8Q...

4) Back in Import Fixer, select the IT & IAT at the top of the window.

5) In the IT & IAT window select everything under the Code sections and click Get Imports (auto scan)

It should look like this

6) Select Clear Imports clearing all the incorrect imports, under IAT manual adding enter the New IAT VA (0x03910410) from UIF minus it's IAT size (0x410) for the VA address and add 410 for the size below.
- VA: 03910000
- Size: 410
Click Add and you should see the correct imports added as shown below

7) Select Fix dump and use the 5u4n8Q... target file we dumped in step 3 above and you should be rewarded with a message showing that the IAT has been rebuilt.

The file should save as *5u4n8Q.IF.exe.exe and we're done!

8) Because this exe used Delphi7, copy the Delphi7.sig file to the IDA pro signature directory and Open *5u4n8Q.IF.exe.exe inside IDA, just select ok for the warning message about imports

9) As you can see the imports are now showing up along with functions!

10) Looking at the disassembled code however still doesn't look right because we need to apply some sigs.

11) Apply the Delphi 7 and BDS 2005-2007 signatures as shown below. Be sure to apply the Delphi 7 sig first as order seems to matter.

When the Please confirm message box comes up, select Unload library
12) Now the disassembled code looks correct and we have a much better understanding of the malware and we are done.
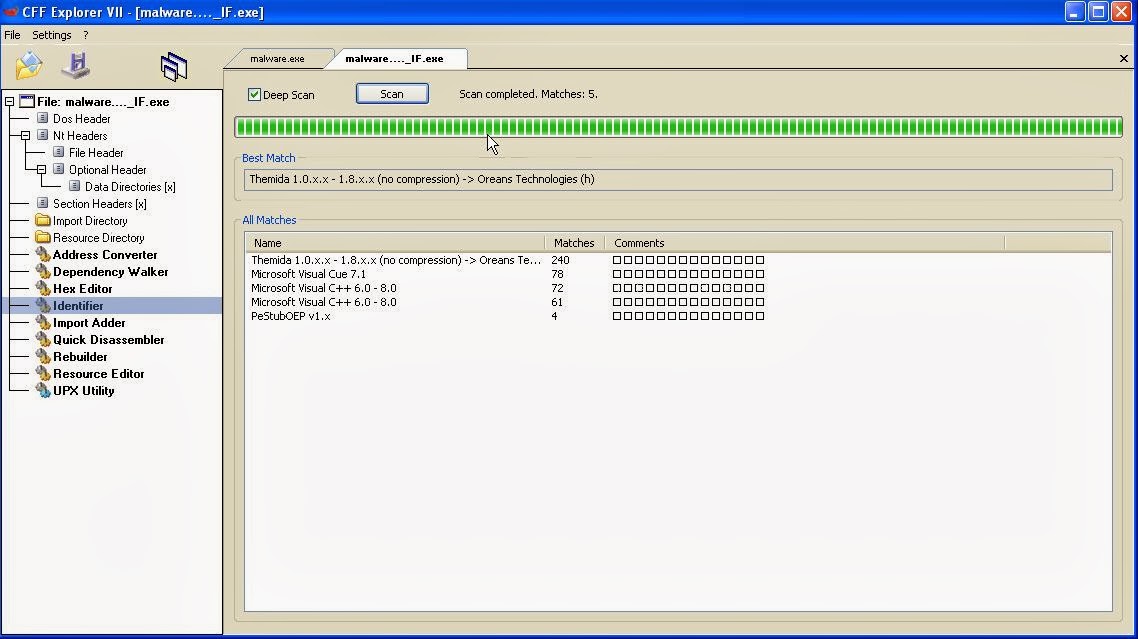
Themida Packed
1) Just to illustrate the difference, here are some screenshots of the malware before we unpacked it and rebuilt the IAT

2) Import Address Table
Qemu Notes
I ran QEMU inside a Windows VM. To transfer files between the Vmware Env and Qemu, enable File sharing on the vmware Windows C drive.Also enable the option that says "Allow network users to change my files"
Inside Qemu just point windows Explore to \\10.0.2.2\c which should be the default gateway and also the Vmware XP image.
This worked against 3 Themida packed malware samples using Themida 2.x.
If anyone has any Themida packed samples, please send them to me or try this process to see if it works.
http://www.offensivecomputing.net/?q=ocsearch
If anyone has any Themida packed samples, please send them to me or try this process to see if it works.
http://www.offensivecomputing.net/?q=ocsearch
MD5:
9a597cae40e4d22695626c84878d80cf SHA1:
850ba4950cc1e9624e85200e48e8a400683ffb12
SHA256:
1129e7372053a9259526b35a41c62373dd1656329287eec69c668252003ec9f8
Original Submitted Filename:
9a597cae40e4d22695626c84878d80cf.exe Date Added:
2009-04-04 04:47:30.931305
Magic File Type:
MS-DOS executable PE for MS Windows (GUI) Intel 80386 32-bit Packer Signature:
9a597cae40e4d22695626c84878d80cf SHA1:
850ba4950cc1e9624e85200e48e8a400683ffb12
SHA256:
1129e7372053a9259526b35a41c62373dd1656329287eec69c668252003ec9f8
Original Submitted Filename:
9a597cae40e4d22695626c84878d80cf.exe Date Added:
2009-04-04 04:47:30.931305
Magic File Type:
MS-DOS executable PE for MS Windows (GUI) Intel 80386 32-bit Packer Signature:
Anti-Virus Results:
BitDefender Trojan.Generic.772406
AVGScan Win32/Themida
Tags:
Add a tag:
BitDefender Trojan.Generic.772406
AVGScan Win32/Themida
Tags:
Add a tag:
This screenshot was taken after using the unpacking methods.
Summary
This attack against this version and implementation of Themida works because we bypass all the protection mechanisms by running the sample in an environment Themida deems as safe. We only need to rebuild the IAT once the sample uncompresses in memory, dump and rebuild the real processes IAT.


.jpg)



Not work this time
ReplyDelete